Description
Your router has been hacked and its DNS settings have been modified to serve malicious contents. DNS records on your wireless router are hijacked. While you browse the web, hackers can freely redirect you from an authentic site to a fake one. Sensitive information such as user names, passwords, and credit card details can be acquired. Your personal data is at risk, and so is the security of all devices connected to this network.
The manual solution is to change the DNS records on your router through its admin interface. Alternatively, you can use our SecureDNS feature to shield yourself from the hijacked DNS servers.
Important:
Before trying to solve this problem, make sure to solve all other router problems detected by Avast. Otherwise the following fix will not be effective.
Solution
Select your router manufacturer to view further instructions on how to fix the problem manually:
Details
DNS (short for Domain Name System) is the "phone book" of the Internet. It's a service that provides names for computers, servers, or any resources connected to the Internet. It translates easily memorized domain names (like www.example.com) to the numerical IP addresses needed to locate the service in the network.
Normally, when you type something like www.my-bank.com in your browser, this is what happens:
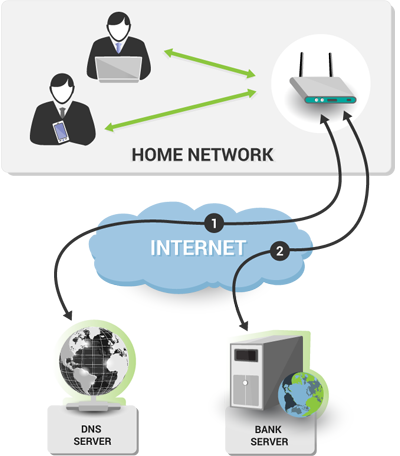
- The browser uses the DNS protocol to ask the DNS server which IP address belongs to www.my-bank.com. The DNS server returns the answer (in the form of the IP address).
- The browser uses that IP address to connect to the bank site.
If the router is infected and the DNS server is hijacked, this is what happens instead:
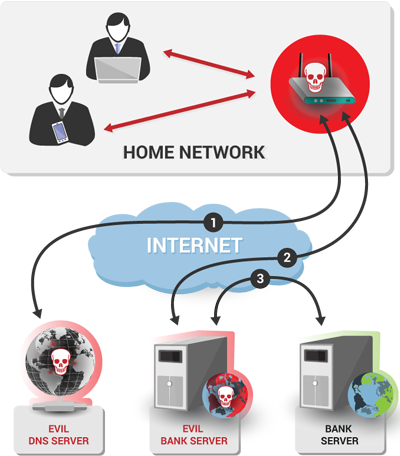
- The browser uses the DNS protocol to ask the DNS server which IP address belongs to www.my-bank.com. However, since the DNS server is controlled by the attacker, it doesn't return the real IP address of the site. Instead, it returns an IP address of a different server that the attacker controls.
- The browser then unknowingly connects to that malicious server instead of the correct one.
- The malicious server then typically uses resources (images, texts, style sheets etc.) from the original server, so that it looks more legitimate.
Instead of connecting to a clean site or service, you'll visit a rogue one where your banking information can be captured. Depending on the skills of the attacker, the rogue server may even use the HTTPS protocol and have SSL certificates that looks genuine to the browser. Therefore, it is very difficult for you, as a user, to detect that there is anything suspicious going on.
In most cases, the remedy is to simply use the DNS servers automatically configured by your Internet provider (via Dynamic Host Configuration Protocol, or DHCP, which dynamically distributes network configuration parameters such as IP addresses). Another possibility is a static value that you assign manually. But first ensure that the router is not vulnerable anymore, otherwise the infection will return.








